为了增强服务器安全性, 需要实现双因子认证, 以便更好的保护自己的账号安全
1. 安装 Google Authenticator
1
2
3
4
5
6
7
8
# debian
$ apt-get update
$ apt-get install libpam-google-authenticator
# redhat
$ yum install google-authenticator
# 根据提示添加令牌, 如果二维码显示不出来, 则使用 token 来添加
$ google-authenticator
2. 配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
# 基于时间生成的令牌
Do you want authentication tokens to be time-based (y/n) y
# 是否更新你的 "~/.google_authenticator" 文件?
Do you want me to update your "~/.google_authenticator" file (y/n) y
# 禁止中间人攻击(秘钥只可以使用一次)
Do you want to disallow multiple uses of the same authentication
token? This restricts you to one login about every 30s, but it increases
your chances to notice or even prevent man-in-the-middle attacks (y/n) y
# 误差范围扩大(系统时间与令牌客户端时间误差)
By default, tokens are good for 30 seconds and in order to compensate for
possible time-skew between the client and the server, we allow an extra
token before and after the current time. If you experience problems with poor
time synchronization, you can increase the window from its default
size of 1:30min to about 4min. Do you want to do so (y/n) n
# 限制登录尝试(如果是局域网开发机器, 不需要开)
If the computer that you are logging into isn't hardened against brute-force
login attempts, you can enable rate-limiting for the authentication module.
By default, this limits attackers to no more than 3 login attempts every 30s.
Do you want to enable rate-limiting (y/n) y
3. 配置 sshd
1
2
3
4
5
6
7
8
9
10
$ sudo vi /etc/ssh/sshd_config
# 打开一次性认证特性
# ChallengeResponseAuthentication yes
$ sudo vi /etc/pam.d/sshd
# 在最后一行增加
# uth required pam_google_authenticator.so
# 保留一个 ssh 连接, 以免配置错误上不去
$ sudo systemctl restart sshd
4. 测试
对于使用公钥认证的情况, 无需测试, 因为公钥认证不会受到双因子认证的限制
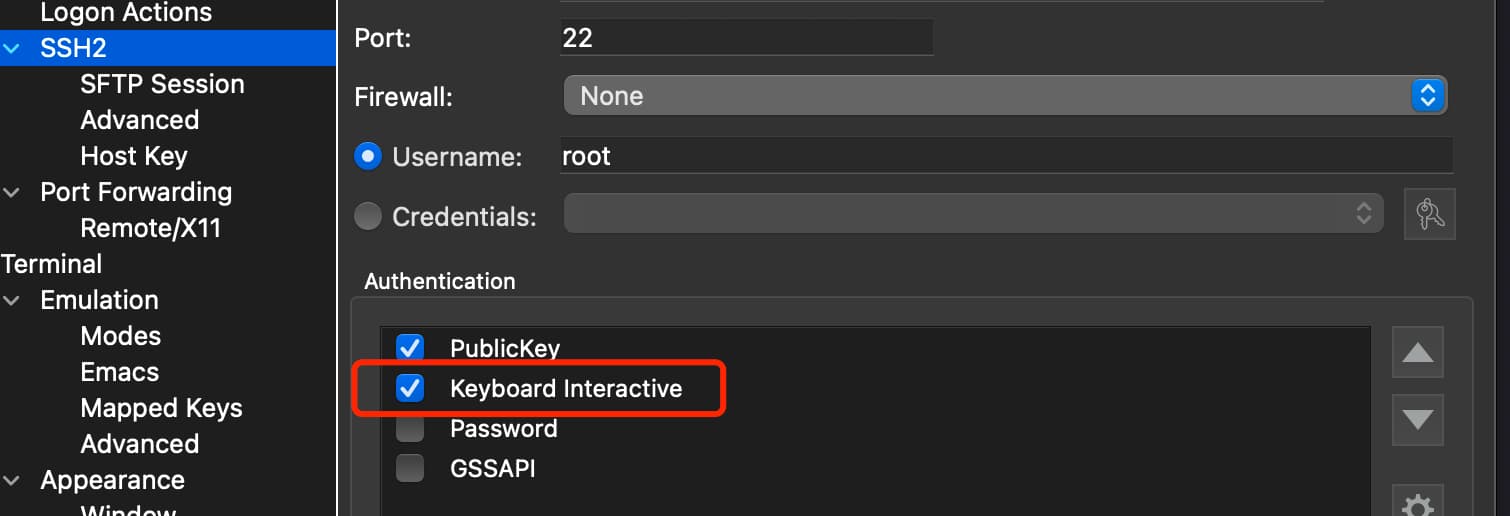
使用账号密码登陆时, 需要在 ssh 客户端配置一下认证方式为下图框选, 否则不能登陆: